Revolutionizing Finance: The Role of Zero Trust Security Strategies
Introduction
The livelihood of financial institutions today, depends heavily on economic trends driven by advanced technologies. In particular, digitalization in the financial sector has made cybersecurity a critical issue.
These range from simple hacks and attacks on customer databases to more complex ransomware attacks and other malware that confront financial organizations. It isn’t just about guarding against the loss of said data; it is about safeguarding the very fabric of customer trust, and therefore business viability.
It becomes clear that classical approaches fail to protect organizations from new threats, which is why the industry looks for new ways, such as cyber security Zero Trust Architecture. This model offers a transformative approach to safeguarding sensitive financial data, focusing on one crucial principle: never trust, always verify.
The Current Landscape of Cybersecurity in Finance
The financial sector is considered to be the most vulnerable to cyber criminals and often suffers cyber attacks due to the rich content of the sector.
The cost of a financial breach is extensive: on average, costs are in the millions due to regulatory fines and probably the loss of consumer confidence. As per the source, financial organizations faced an average of $4.45 million per breach.
Previous security solutions, focusing on a perimeter concept, where firewalls and single-layer authentication are sufficient, are incapable of handling modern advanced threats.
Consequently, financial institutions now experience increasing expense not only in losing data but also in incurring penalties which are assessed; something that has pushed for the need for the establishment of stronger cybersecurity frameworks.
Defining Cyber Security Zero Trust Architecture
The Zero Trust Security model is best characterized as a model of constant suspicion in information security.
In contrast to the traditional approach of utilizing location and device information to give user accounts permissions, the cyber security Zero Trust model is based on the main concept of never trust, always check.
What this means is that every user and device must always prove who they are and what they want to do even if they are already inside the network.
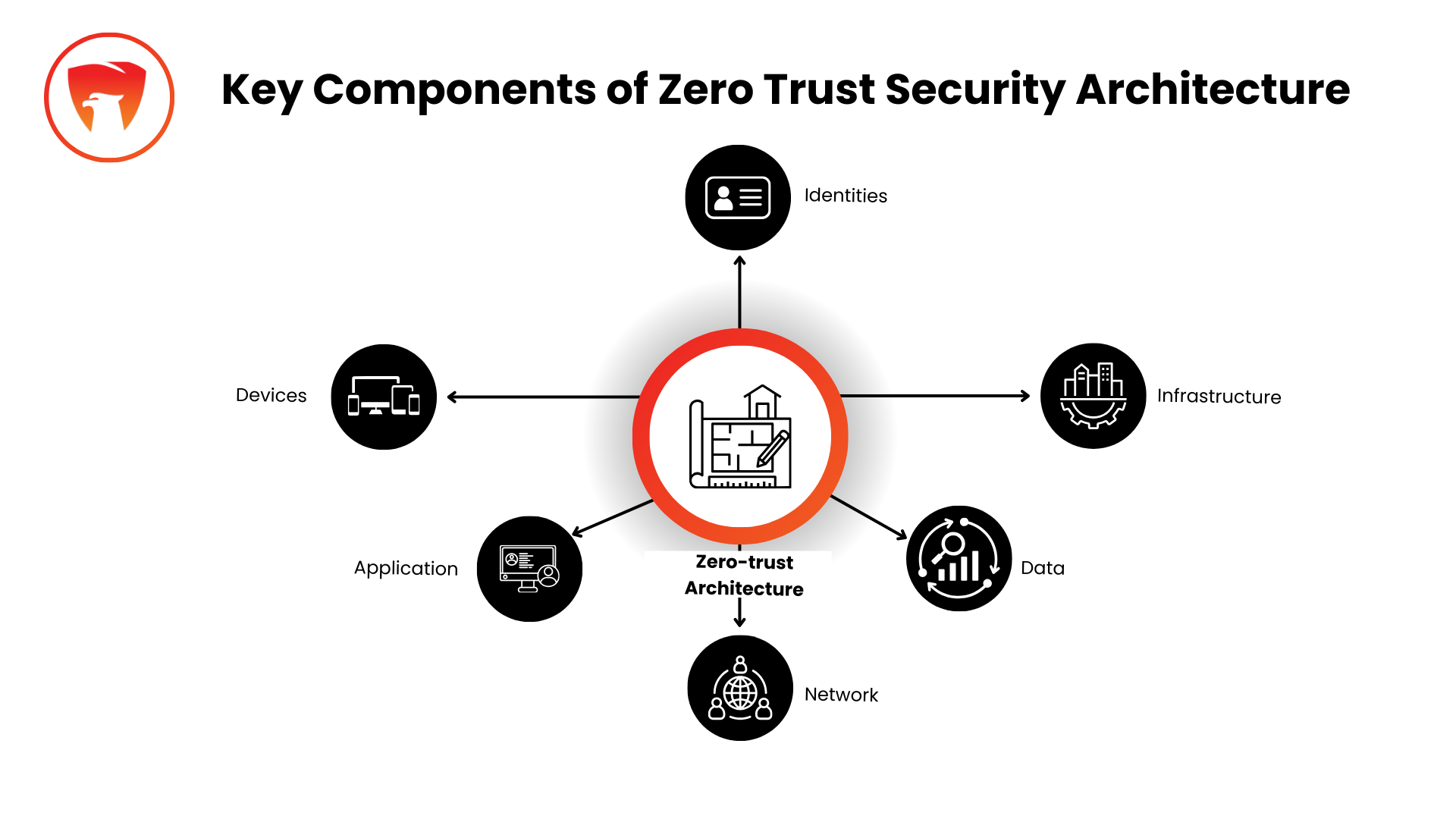
Key Components of Zero Trust Security Architecture
At the core of cyber security Zero Trust Architecture are several key components.
-
User Identity Verification: The second is to limit the number of people who can access limited resources mainly as a security feature.
-
Device Trust Validation: Confirming the security status of each machine when the user seeks to log in to the network.
-
Least Privilege Access Control: Restrict the user to only those data and applications they need in his / her working capacity.
-
Network Segmentation: Partitioning of networks reduces the chances of break and the ability of the break to affect a large area.
-
Continuous Monitoring and Analytics: Real-time capability of monitoring access patterns and ability to identify threats.
Unlike previous models, this model reduces the concept of access and focuses on constant validation, making it a perfect fit for the financial institution to deal with the various problems. At HawkShield we follow these to help businesses safeguard their data everywhere, and anywhere.
Challenges in Implementing Zero Trust in Finance
Analyzing the barriers and processes behind the Zero Trust Security Framework when applied to finance, it has been found that the primary challenges relate to the organizational culture and the IT environment.
Financial institutions need to also look at costs and how they are going to implement and recover them, they also need to ensure their employees are informed of the new security measures.
These challenges mean that a multitude of strategies must be in place for organizations to implement Zero Trust in the sector.
-
Resistance to change within organizational culture
Moving towards cybersecurity Zero Trust Architecture is a radical paradigm shift at best in regards to security.
Most of the banks and financial companies around the world migrating from classic perimeter protection models might experience internal challenges because of the new constant and strenuous methods of identification that Zero Trust involves.
-
The complexity of existing IT systems
Traditional large financial institutions tend to have deeply layered and growing IT architectures, with core legacy systems that are difficult to bring under the Zero Trust model.
Integrating the older systems with the fundamental goals of the Zero Trust model, like continuous authentication, micro-segmentation of the network, etc., is not a simple task as it may imply major redirects, in terms of architecture, for enterprises, which makes the process intricate and lengthy at the same time.
-
Potential costs and resource allocation concerns
Zero Trust Reference Architecture entails applying new security technologies, including identity protection, monitoring tools, and secure access solutions.
Others include initial and ongoing costs of infrastructure and implementation together with time and resources that might be required should an organization opt for a phased approach to implementation, some of which may be financially demanding and may force financial institutions to think twice before spending on security in the manner they prefer.
-
Need for employee training and awareness
That is why a successful Zero Trust model does not work only with technology, but also with the security of staff. The employees have to be trained regarding the concept of cybersecurity Zero Trust Architecture, including the framework of principles like “least privilege access”, and constant checking.
That way, compliance is maintained across different teams, and everyone becomes security-minded, but it takes time and regular reinforcement to keep it up.
Solution Approach: Implementing Zero Trust Security
To fortify organizational security, implementing Zero Trust in financial institutions is essential. This approach demands a phased, strategic roll-out to ensure comprehensive protection.
To create a mechanism to bolster the financial organization's defense, it must be understood that: An evaluation of the current security status is necessary to identify the vulnerabilities that need to be addressed.
An implementation plan can be split up into smaller phases to reach the goal A CALL can be made to establish the need for the solution and provide the necessary support to get the financial organization's buy-in Investments must be made in technologies that can help improve the current situation.
This gives them a structured way of doing things which will help them create a solid security posture that is based on the zero-trust model.
How to implement Zero Trust in financial institutions
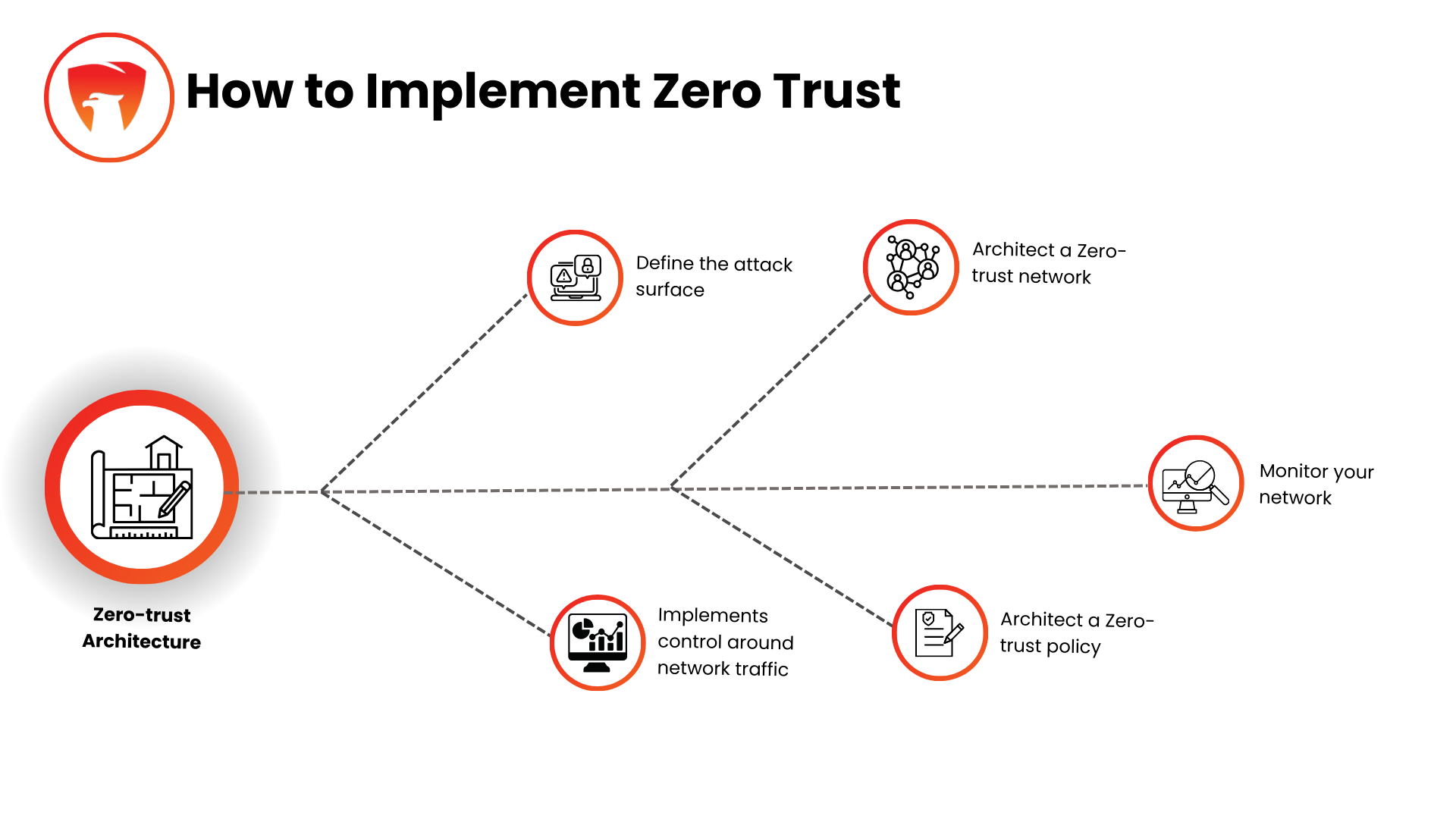
To implement Zero Trust Security effectively, Hawkshield suggests a step-by-step approach for financial institutions. Our tailored strategies and ongoing support ensure a smooth transition, allowing organizations to adopt Zero Trust principles while enhancing their security posture.
-
Assessing current security posture
The first activity is to conduct a current state assessment of the security architecture to determine where and how cybersecurity Zero Trust Architecture can help close the security gaps.
One can identify these dangers and then allocate resources effectively when an assessment of the security status is conducted comprehensively.
-
Developing a phased implementation plan
Achieving Zero Trust is not an overnight process. A phased implementation plan helps institutions approach the Zero Trust model systematically as each phase will focus on a critical area for implementation before moving to the other area.
The approach is of benefit in preventing interruption and affords assemblage time to make changes.
-
Collaborating with stakeholders and obtaining buy-in
Successful Zero Trust Architecture requires support from the company’s core and all organizational levels.
In engaging other stakeholders such as IT, management, and the end users, institutions are able to get the much-needed buy-in, manage emerging concerns, and more importantly align expectations towards appreciating the multi-faceted gains of institutional security through the Zero Trust model.
-
Investing in the right technologies
Zero Trust is based on the use of sophisticated technologies for the permanent check of identities and strict access regulation.
The financial institutions have to implement Identity Management solutions, access controls, and monitoring to honor the “never trust, always verify” approach of the model. These technologies help to achieve the level of granularity, constant monitoring, and rapid threat response required in a robust Zero Trust model.
Benefits of Zero Trust Security in Finance
Zero Trust Security can provide financial institutions with the following benefits: Strong access control reduces the risk of data breaches, compliance benefits with regulations, and customer trust through the safeguarding of data.
Furthermore, continuous monitoring provides the same metrics on which preventive changes can be made, and that is why the cyber security Zero Trust Architecture is so effective in enhancing security in the field of finance.
-
Enhanced protection against data breaches
It enunciates the ‘never trust, always verify’ concept, making it harder for potential threat actors to sneak in and compromise the system.
Even if an attacker gets past one barrier, he has no open playing field ahead of him, and his range of maneuver is severely circumscribed, which significantly reduces the harm he can do.
-
Improved regulatory compliance
As a matter of fact, financial institutions are subject to high, and strict requirements for data protection.
Zero Trust therefore enhances compliance since the access controls protocols and real-time monitoring it incorporates adhere to best industry practices as well as legal requirements. Not only that but achieving compliance also ensures that the company does not incur severe penalties besides addressing new security requirements all the time.
-
Increased customer trust and reputation
Money matters especially require trust which in finance is viewed as sacred. Customers have a demand that their information should be safeguarded from unauthorized access.
With Zero Trust implementation, financial organizations can guarantee the clients that their data is secure, thus improving the customers’ trust in the institution and, in effect, protecting the financial institution’s reputation.
-
Data-driven insights for continuous improvement
Being the architecture of constant observation and analysis, Zero Trust generates useful information about access behaviors and security incidents in financial organizations, allowing these institutions to detect possible threats and enhance their security readiness.
They assist in the better development of security approaches and predicting emergent threats and potential future challenges, enhancing security systematically.
How Hawkshield Can Help
At HawkShield, our motto is “Never trust, always verify.” Insider threats are more fatal, as they are hard to predict. But with HawkShield’s services that are mainly based on cyber security Zero Trust Architecture, user identification and management systems have several layers of security.
That means, even if a breach is happening at a single layer, several other layers are present to authenticate or verify and provide complete security.
Also, with advanced threat detection and response capabilities of AI/ML Scrutinization, a potential threat can be prohibited even before it takes place.
Email Protection, Browser Protection, Data Security Posture Management (DSPM), Data Classification, and Data Discovery your data and finances will be safe all the time. Tailored policies will take care of the security needs of every company individually because every business is unique.
At HawkShield we are not done by just offering you the services, at every step of the implementation process we will be with you as your guiding angel. Clients are our top priority, so from implementing the security measures to ensuring a smooth run, we will be with you so that you can focus on your business 100%.
Conclusion
Zero Trust Security can be considered as a brand new approach to cybersecurity in the financial sector. Proactively developing an organization's continuous checks and the principle of minimal rights can help financial institutions construct stronger security and protection models that will not only protect their resources but also gain the trust of customers.
Singapore also shows that in a world with high stakes and continuous threats, cyber security Zero Trust Architecture is the realistic paradigm for building a more secure and trustworthy financial sector worldwide.
However, implementing a new technology is not easy, and that is why HawkShield is ready to support you with its top-notch solutions. Schedule a demo and check it yourself.



 By HawkShield
By HawkShield